In today's rapidly evolving digital landscape, cloud computing stands as a transformative force, reshaping the way businesses operate and individuals access information. Navigating the cloud effectively is crucial for harnessing its full potential.
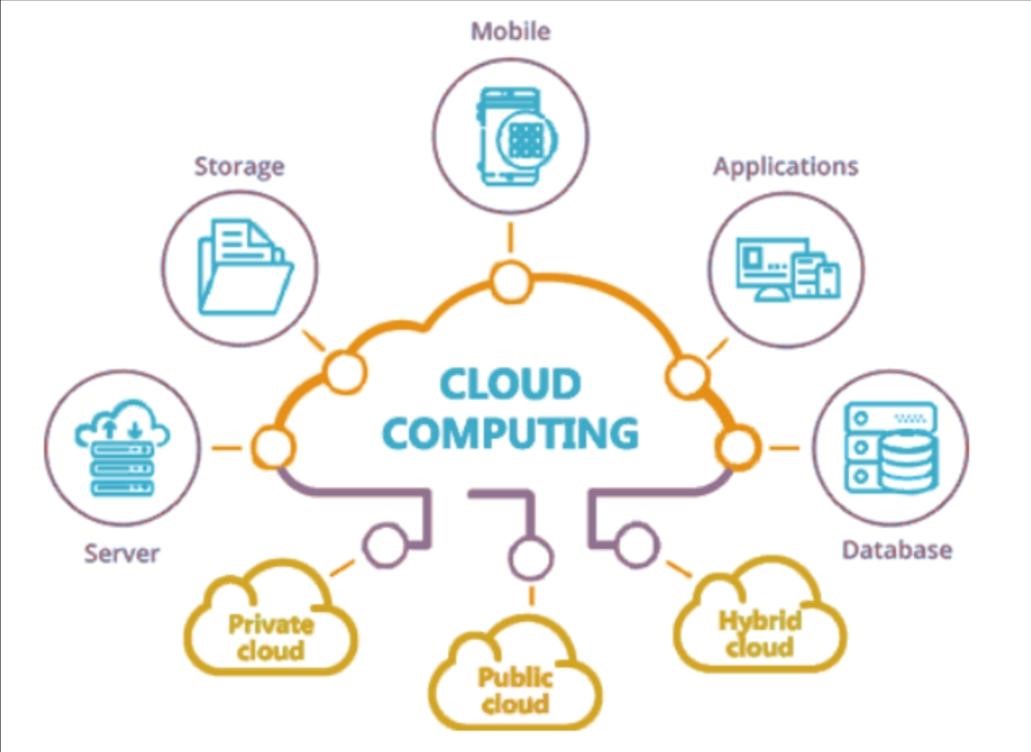
Cloud computing is a revolutionary paradigm in information technology that fundamentally transforms the way computing resources are provisioned, accessed, and managed. Rather than relying on traditional on-premises infrastructure, cloud computing leverages a network of remote servers hosted on the internet to store, manage, and process data. It provides users with on-demand access to a vast array of computing resources, including storage, processing power, and applications, without the need for significant upfront investments in physical hardware.
Key characteristics of cloud computing include on-demand resource provisioning, broad network access, rapid elasticity to scale resources up or down as needed, and measured service where usage is monitored and billed accordingly.
Cloud computing is typically categorized into three service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). It also encompasses deployment models like public cloud, private cloud, hybrid cloud, and multicloud strategies, providing flexibility for diverse business requirements.
Break down Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) to understand their unique benefits.
Infrastructure as a Service (IaaS):
Provides virtualized computing resources over the internet, including virtual machines, storage, and networks. Users have control over the operating system, applications, and some networking components.
Platform as a Service (PaaS):
Offers a platform allowing users to develop, run, and manage applications without dealing with the complexities of underlying infrastructure. It includes tools for development, testing, and deployment.
Software as a Service (SaaS):
Delivers software applications over the internet on a subscription basis. Users can access the software through a web browser without the need for installation or maintenance.
Function as a Service (FaaS) or Serverless Computing:
Enables developers to execute individual functions or pieces of code in response to events without managing the underlying infrastructure. Users only pay for the computing resources used during the execution of functions.
Database as a Service (DBaaS):
Provides database management and maintenance as a cloud service. Users can access and manage databases without the need to handle the operational aspects like backups and updates.
Container as a Service (CaaS):
Offers a platform for deploying, managing, and scaling containerized applications. It simplifies the orchestration and management of containerized environments.
Desktop as a Service (DaaS):
Delivers virtual desktop environments over the internet, allowing users to access their desktops and applications from any device with an internet connection.
Network as a Service (NaaS):
Provides network infrastructure and services on a subscription basis. Users can access and manage networking resources, such as bandwidth and virtual networks, without owning the physical infrastructure.
These cloud service models cater to different needs, allowing organizations to choose the level of abstraction and management control that aligns with their specific requirements.
Delve into the pros and cons of public, private, and hybrid cloud models, helping you make informed decisions based on your specific needs.
Public Cloud:
Description: Services are offered by third-party providers and are available to the public over the internet. Resources are shared among multiple users.
Advantages: Cost-effective, scalable, no need for on-premises hardware management, and accessible from anywhere.
Use Cases: Ideal for startups, small businesses, and applications with variable workloads.
Private Cloud:
Description: Infrastructure is dedicated to a single organization and can be hosted on-premises or by a third-party provider. Offers more control over security and customization.
Advantages: Enhanced security, greater control over resources, and tailored to specific organizational needs.
Use Cases: Suitable for industries with strict compliance requirements, sensitive data, or organizations with specific customization needs.
Hybrid Cloud:
Description: Combines elements of both public and private clouds, allowing data and applications to be shared between them. Provides flexibility to move workloads based on requirements.
Advantages: Balances scalability and control, flexibility to adapt to changing needs, and facilitates a gradual transition to the cloud.
Use Cases: Useful for organizations with dynamic workloads, sensitive data that requires private infrastructure, and the need for burst capacity.
Choosing between public, private, or hybrid cloud depends on factors such as data sensitivity, compliance requirements, scalability needs, and budget considerations. Each model has its own strengths, and the optimal solution often involves a strategic combination based on specific business requirements.
Learn how cloud solutions provide scalability and elasticity, enabling businesses to adapt to changing demands seamlessly. Security in the Cloud
Scalability:
Scalability in cloud computing refers to the ability of a system or application to handle an increasing amount of workload or demand. It can be achieved by adding resources to the existing infrastructure, such as adding more servers, storage, or network capacity. Scalability ensures that as user or data demands grow, the system can expand its resources to maintain performance, responsiveness, and overall efficiency.
Elasticity:
Elasticity is an aspect of scalability that specifically emphasizes the dynamic allocation and deallocation of resources in real-time based on demand. It enables a system to automatically scale up or down, responding to fluctuations in workload. Cloud services often provide elastic capabilities, allowing users to seamlessly adjust resources in alignment with varying requirements. Elasticity ensures efficient resource utilization, cost-effectiveness, and the ability to adapt rapidly to changing workloads.
Data Security and Compliance
Address common concerns surrounding data security in the cloud and explore compliance measures to safeguard sensitive information.
Data Security in Cloud Computing:
Encryption:
Implement end-to-end encryption to protect data during transmission and storage, ensuring that only authorized parties can access it.
Access Controls:
Utilize robust identity and access management (IAM) solutions to control and monitor access to cloud resources, ensuring only authorized users have appropriate permissions.
Data Backup and Recovery:
Regularly back up data and implement robust recovery mechanisms to safeguard against data loss due to unforeseen events or security breaches.
Security Protocols:
Adhere to industry-standard security protocols and best practices, such as secure sockets layer (SSL) for web communication and multi-factor authentication (MFA) for enhanced user verification.
Compliance in Cloud Computing:
Regulatory Compliance:
Stay informed and comply with industry-specific regulations and standards relevant to your business, such as GDPR, HIPAA, or PCI DSS, to avoid legal and financial repercussions.
Audit Trails:
Implement audit trails and logging mechanisms to track user activities and changes within the cloud environment, aiding in compliance verification and forensic analysis.
Data Residency and Jurisdiction:
Be mindful of data residency requirements and legal jurisdictions when storing and processing data in the cloud, ensuring alignment with regional and international laws.
Regular Audits and Assessments:
Conduct regular security audits and assessments, either internally or through third-party services, to identify and address potential vulnerabilities and ensure ongoing compliance.
Balancing robust data security measures with adherence to compliance standards is essential for organizations leveraging cloud computing. Implementing a comprehensive strategy that includes encryption, access controls, regular audits, and compliance monitoring helps mitigate risks and ensures a secure and compliant cloud environment.
In conclusion, navigating the cloud requires a thoughtful approach that encompasses a deep understanding of cloud computing fundamentals, strategic decision-making, and a commitment to security and compliance. The journey through the cloud involves exploring different service models such as IaaS, PaaS, and SaaS, as well as choosing between deployment options like public, private, or hybrid cloud.
The scalability and elasticity offered by cloud computing enable organizations to adapt to changing workloads efficiently. It is crucial to leverage these capabilities to optimize resource usage and ensure cost-effectiveness. Additionally, embracing the cloud involves addressing data security concerns through encryption, access controls, and robust backup mechanisms.
Furthermore, compliance with industry regulations and standards is paramount. Organizations must stay abreast of legal requirements, implement audit trails, and conduct regular assessments to maintain a secure and compliant cloud environment.
As cloud technologies continue to evolve, it is imperative to keep learning and adapting to emerging trends such as serverless architecture and edge computing. Continuous education and staying informed about advancements in the cloud landscape will empower individuals and businesses to unlock the full potential of cloud computing, driving innovation and efficiency in the digital era.
Embark on this journey through the cloud, equipped with the knowledge and insights needed to make informed decisions and harness the full potential of cloud computing in your endeavors.
Author
LAKSHMI POORANI S - CSE
2024-02-23