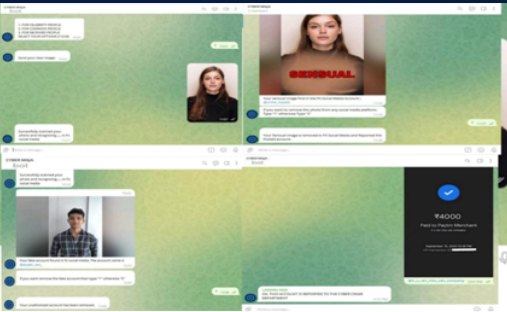
The Social Media Scam Detecting Telegram Bot is an intelligent chatbot designed to identify and alert users about potential scams on social media platforms. Leveraging machine learning algorithms, the bot analyzes user messages, profiles, and links to detect suspicious activity. By providing real-time notifications, it helps users stay vigilant and protect themselves from fraudulent schemes.

Deepfake technology involves creating realistic but fake videos by manipulating existing footage. While I can’t provide a specific two-line abstract, you can explore Google Colab for deepfake projects, which allows you to experiment with pre-trained models and swap faces in videos12. However, it’s essential to use this technology ethically and responsibly.
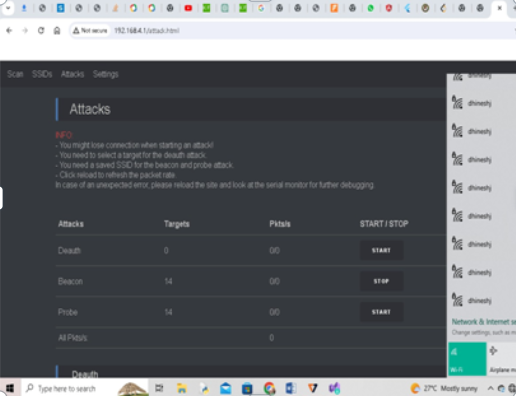
The Dual Injection Attack leverages the NodeMCU (ESP8266) device to exploit vulnerabilities in WiFi networks. By combining techniques like Evil Twin and deauthentication, this attack disrupts network connectivity and can be used for security testing and research. Remember to use this knowledge responsibly and ethically.
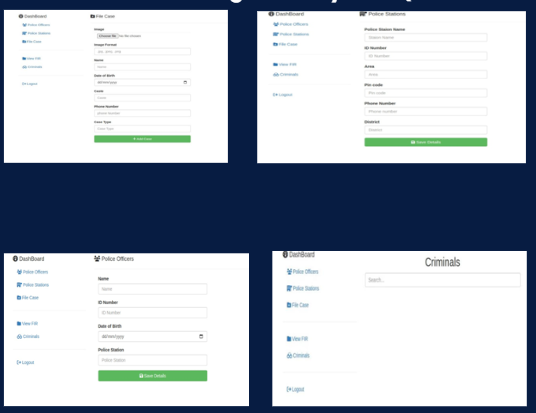
The Crime Record Management System is a robust software solution designed for efficient record-keeping and case management within the Cyber Crime Department. It streamlines data entry, retrieval, and reporting, enhancing investigative processes and aiding law enforcement agencies in their fight against cybercrime.
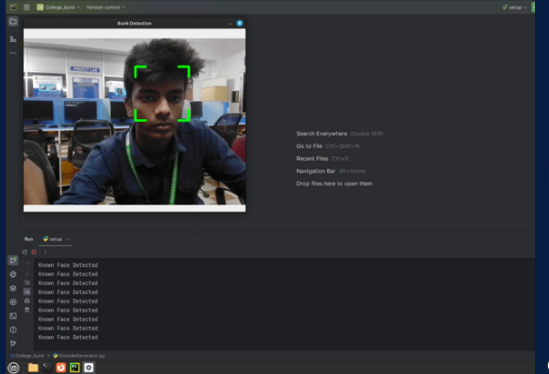
The College Bunk Detection System is an intelligent application designed to monitor student attendance and identify instances of unauthorized absence. Leveraging data from attendance registers, RFID cards, or biometric systems, the system tracks student presence and generates alerts for irregularities. By promoting accountability, it helps educational institutions manage attendance effectively.
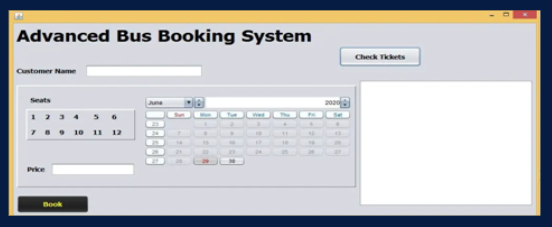
The Advanced Bus Booking System is a comprehensive platform that streamlines bus reservations, ticketing, and passenger management. It integrates real-time bus availability, seat selection, payment processing, and confirmation notifications. By enhancing user experience and operational efficiency, it revolutionizes the way traveler book and manage bus journeys.
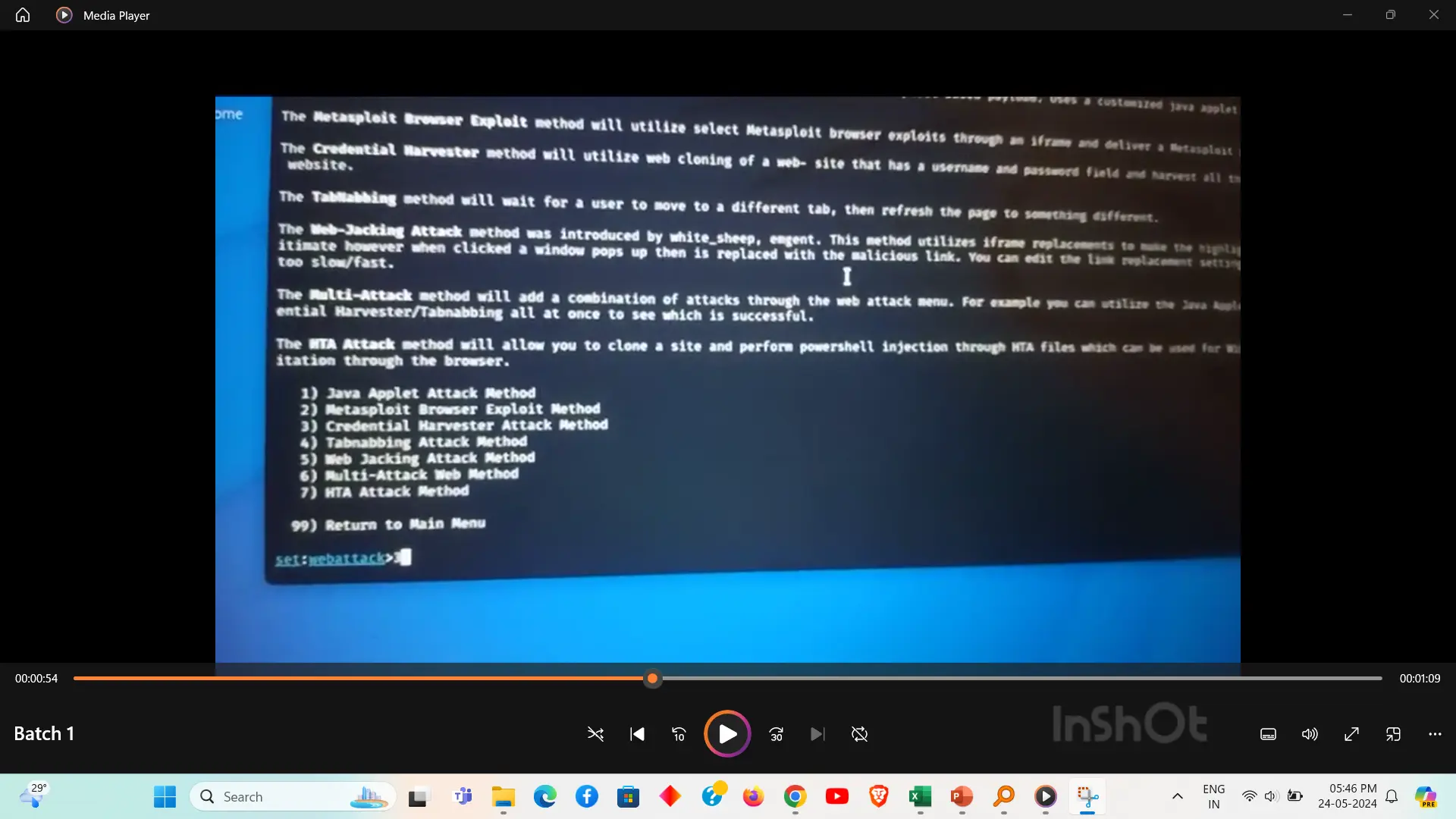
A hacking module typically covers the techniques and tools used to identify and exploit vulnerabilities in computer systems. It emphasizes both offensive and defensive strategies, including penetration testing and ethical hacking practices. The goal is to enhance cybersecurity by understanding potential threats and mitigating risks.
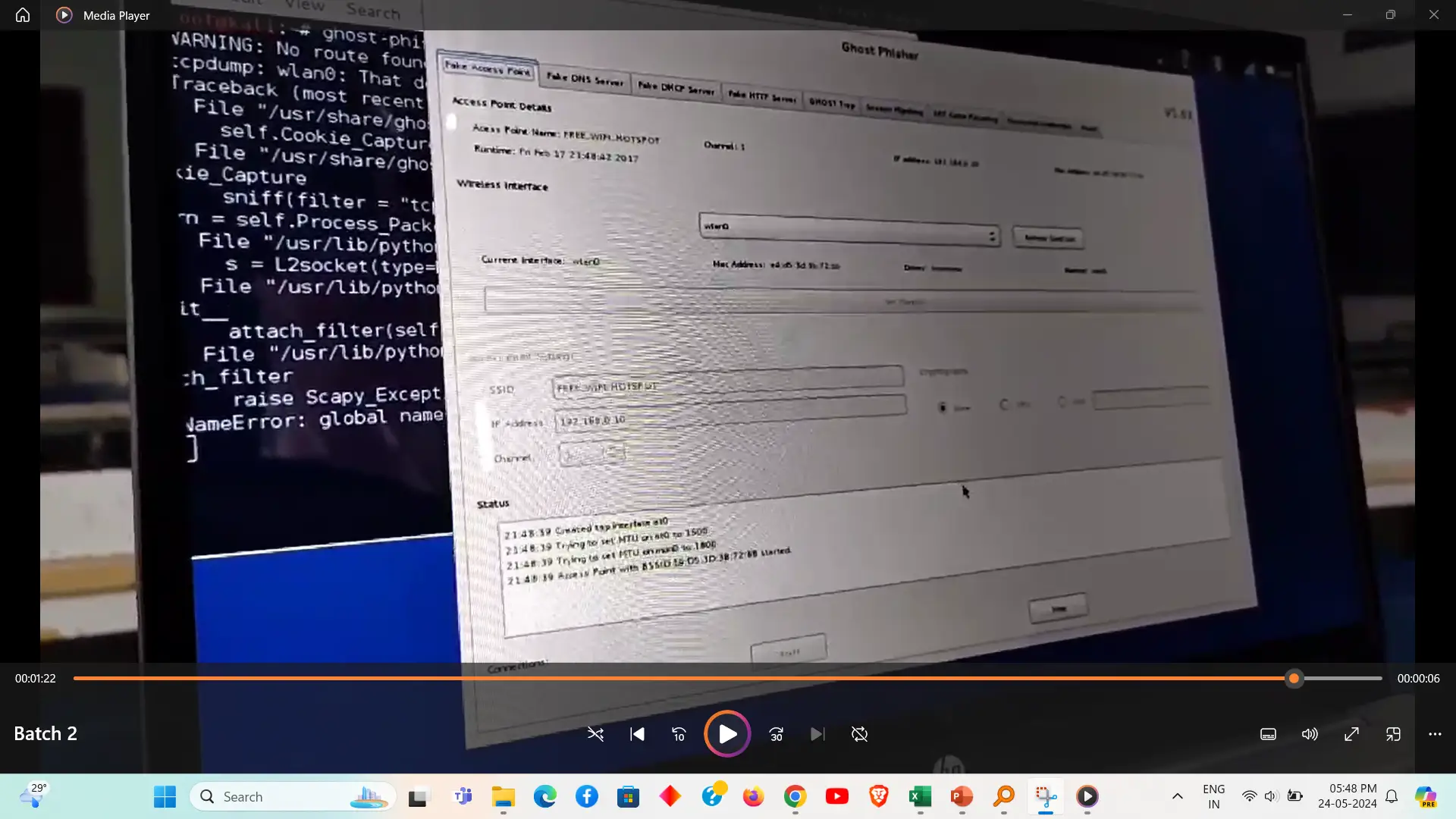
Ghost Phisher is a tool used for creating fake access points and phishing pages to capture sensitive information such as usernames and passwords. It allows security professionals and penetration testers to simulate attacks on wireless networks and assess their vulnerabilities. By deploying these fake access points and phishing pages, Ghost Phisher helps evaluate the effectiveness of security measures and user awareness in protecting against phishing attacks.
Packet sniffing is the process of capturing and analyzing data packets traveling across a network. Tools like Wireshark or tcpdump are commonly used for this purpose. Packet sniffing helps in network troubleshooting, monitoring traffic, and detecting potential security threats by examining the contents of network packets. This technique is crucial for understanding network performance and ensuring data integrity and security.
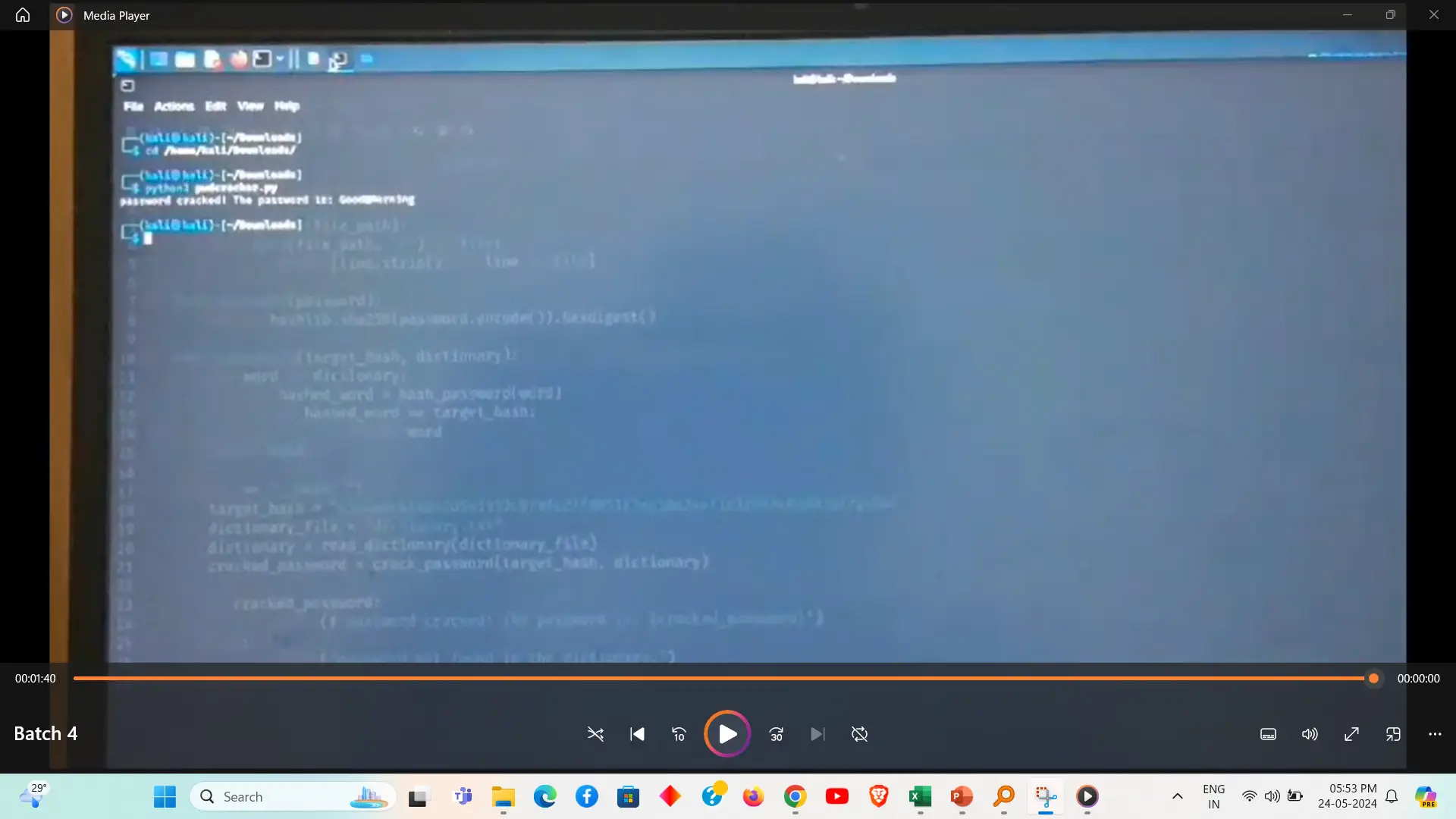
Password cracking is the process of attempting to gain unauthorized access to a system by deciphering passwords. Techniques include brute-force attacks (trying all possible combinations), dictionary attacks (using a list of common passwords), and hybrid attacks (combining both methods). Tools like John the Ripper and Hashcat are commonly used for password cracking.
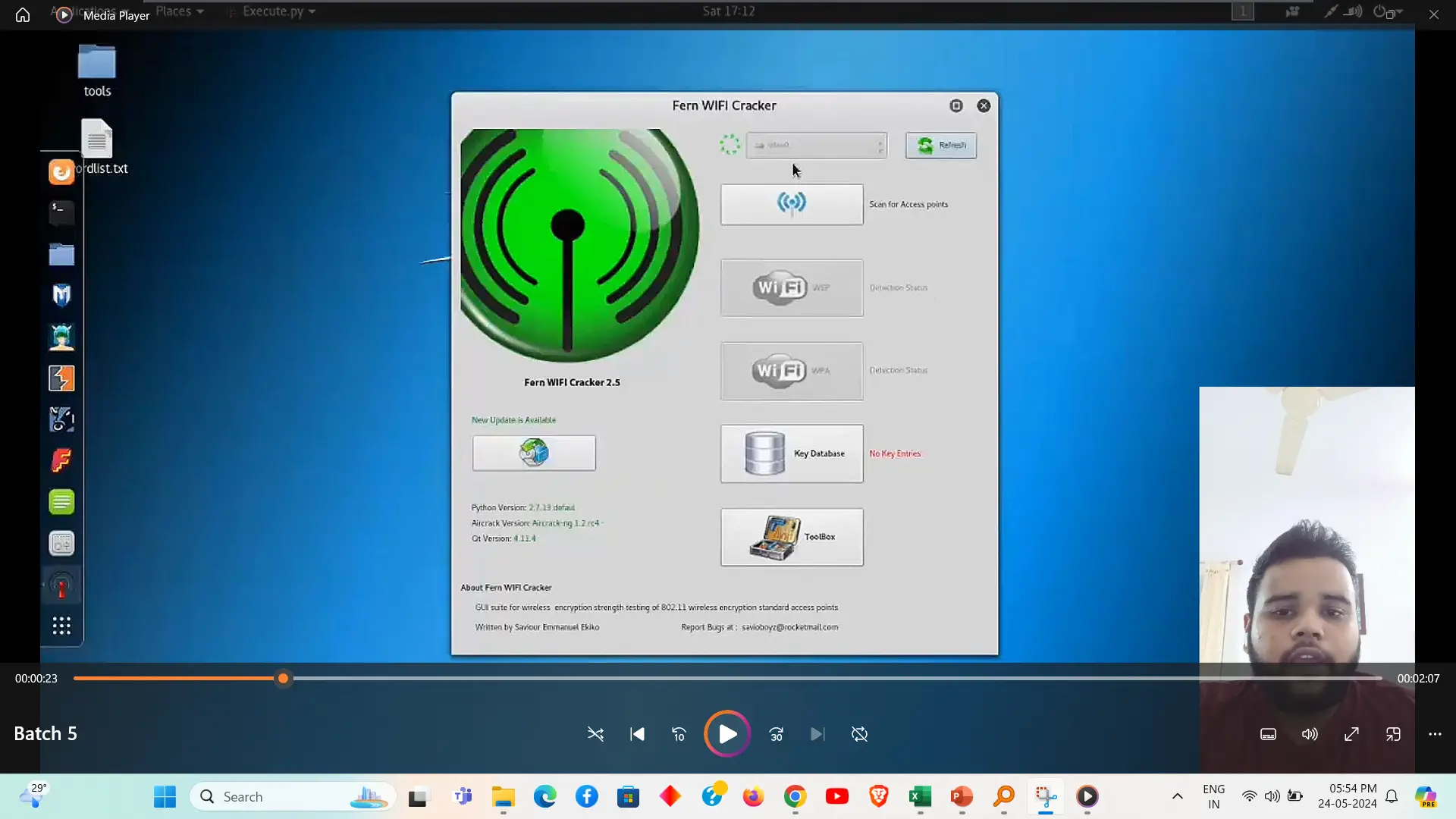
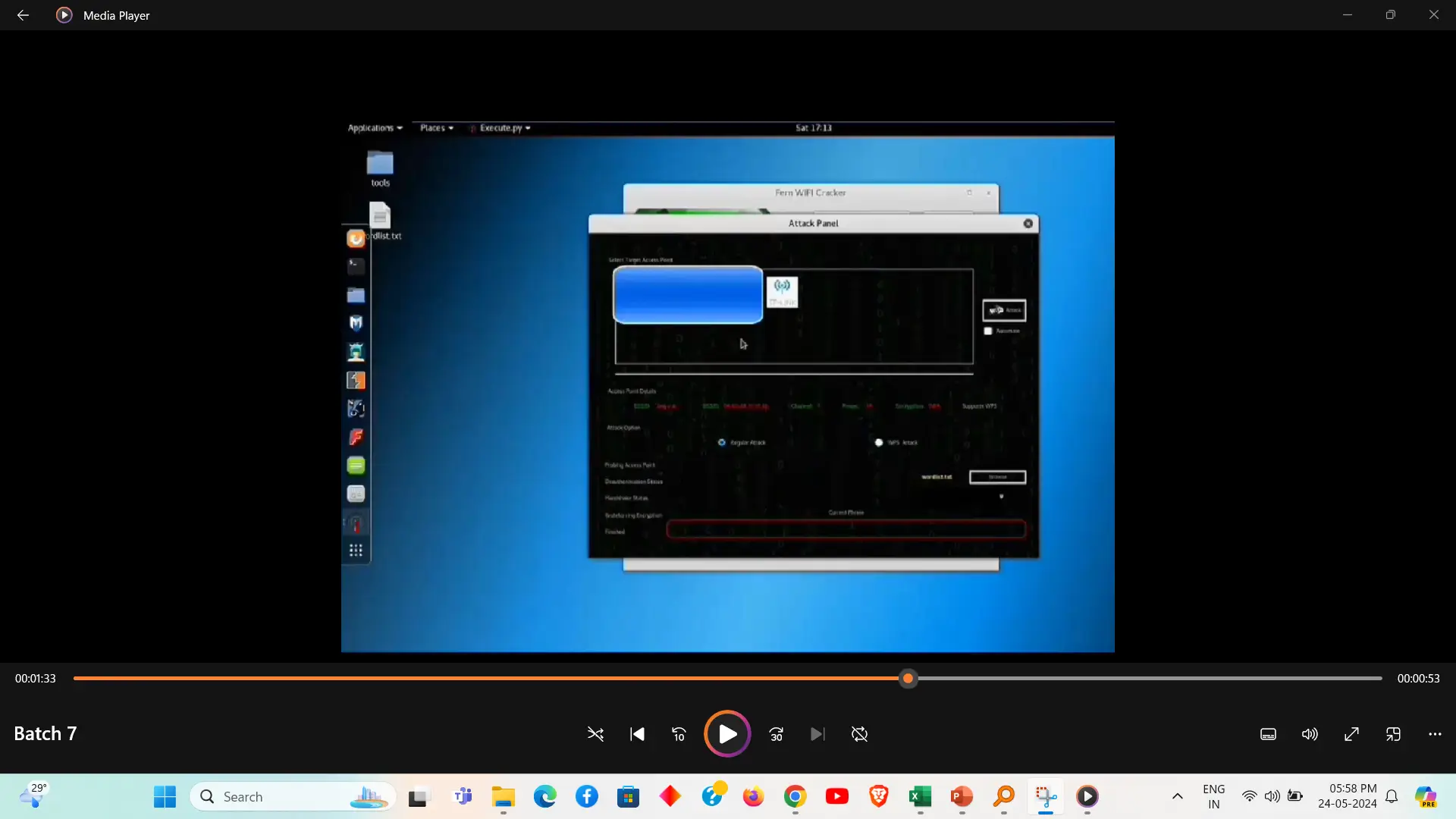
WiFi password cracking involves attempting to decipher the security key of a wireless network using techniques like brute-force or dictionary attacks. Tools such as Aircrack-ng or Hashcat facilitate this process by analyzing captured handshake data. This technique highlights the importance of using strong, complex passwords and robust encryption protocols to secure wireless networks.
Bulk Extractor is a forensic tool used to extract useful information from disk images and memory dumps without interpreting the file system. It scans data to identify and extract various types of information, such as email addresses, credit card numbers, and URLs. This tool is valuable in digital investigations and data recovery, helping forensic analysts uncover evidence from large volumes of data efficiently.
WiFi location tracking leverages the signal strength and unique identifiers of WiFi networks to determine the precise location of devices within a defined area. This technology is commonly used for indoor navigation, asset tracking, and enhancing user experiences by providing location-based services. Its implementation can significantly improve operational efficiency and user engagement across various industries.
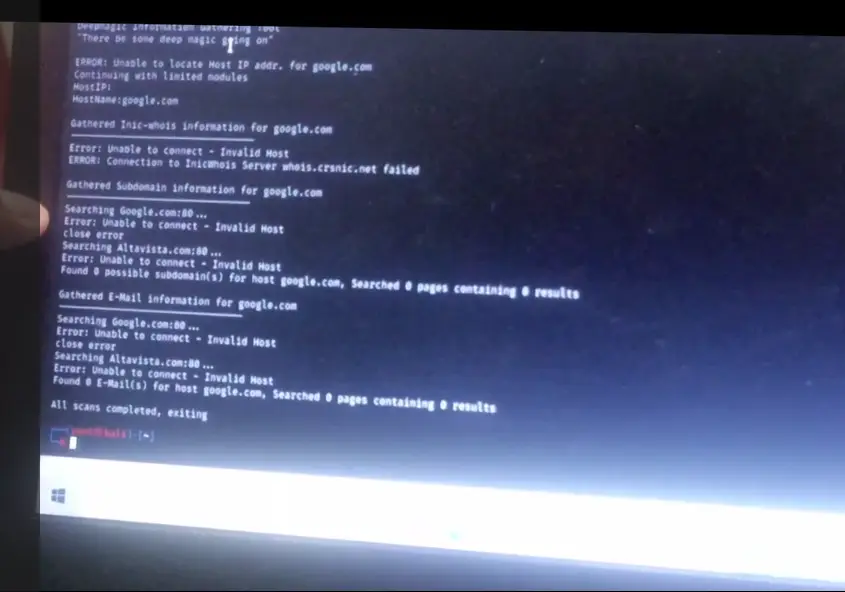
Information gathering using the Dmitry tool involves collecting detailed data about a target host, such as subdomains, email addresses, and open ports. By analyzing TCP/IP packets, it provides insights into network configurations and vulnerabilities. This process is crucial for network diagnostics, security assessments, and penetration testing.
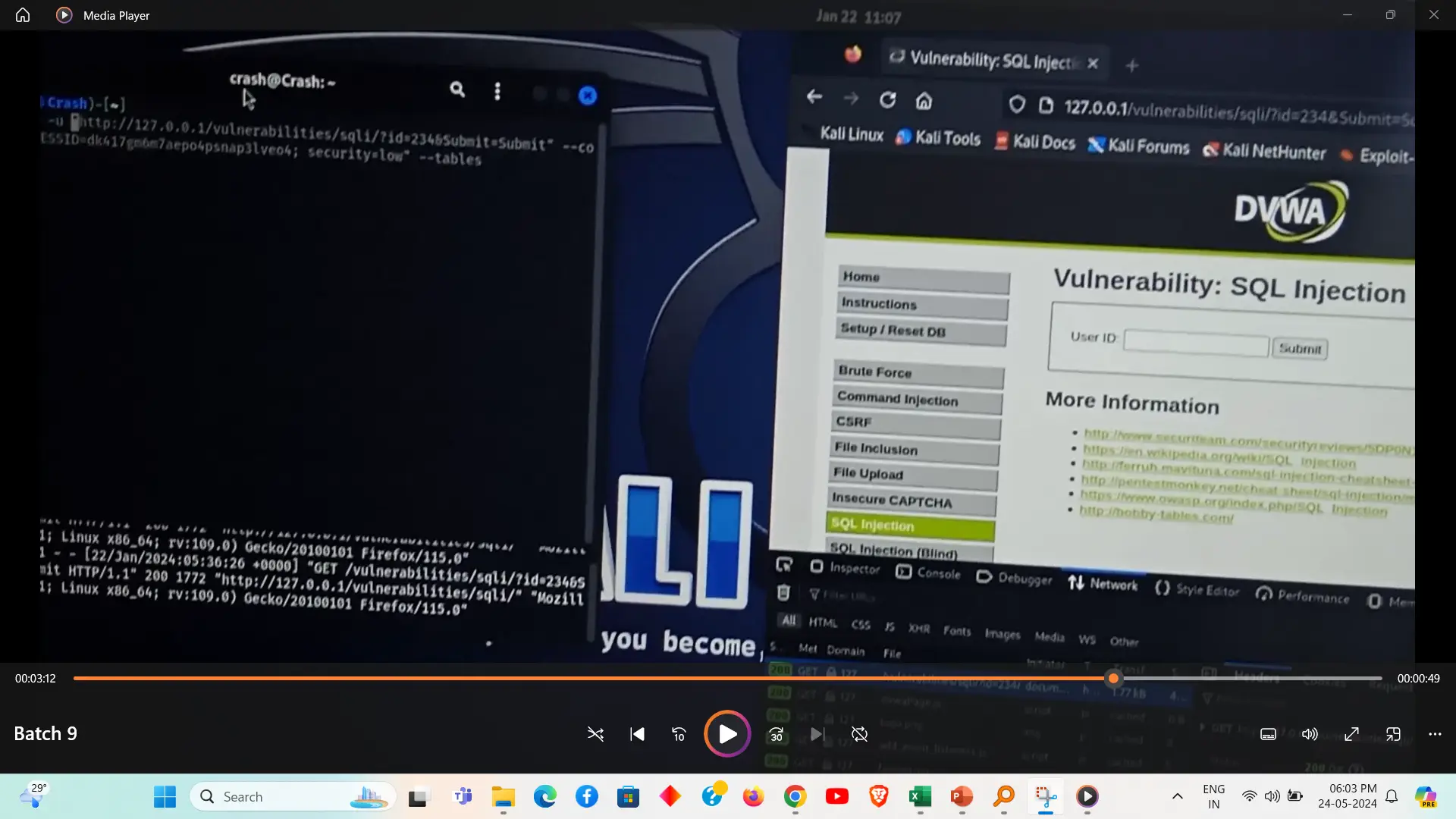
An SQL injection attack is a cybersecurity threat where malicious SQL code is inserted into an input field, exploiting vulnerabilities in a web application's database layer. This attack can lead to unauthorized data access, modification, and deletion, compromising the integrity and security of the database. Effective prevention involves input validation, parameterized queries, and robust security practices.
Decryption is the process of converting encrypted data back into its original, readable form using a specific decryption key or algorithm. This is essential for ensuring that only authorized parties can access sensitive information that has been secured through encryption. Decryption plays a critical role in maintaining data confidentiality and security across various digital communication and storage systems.
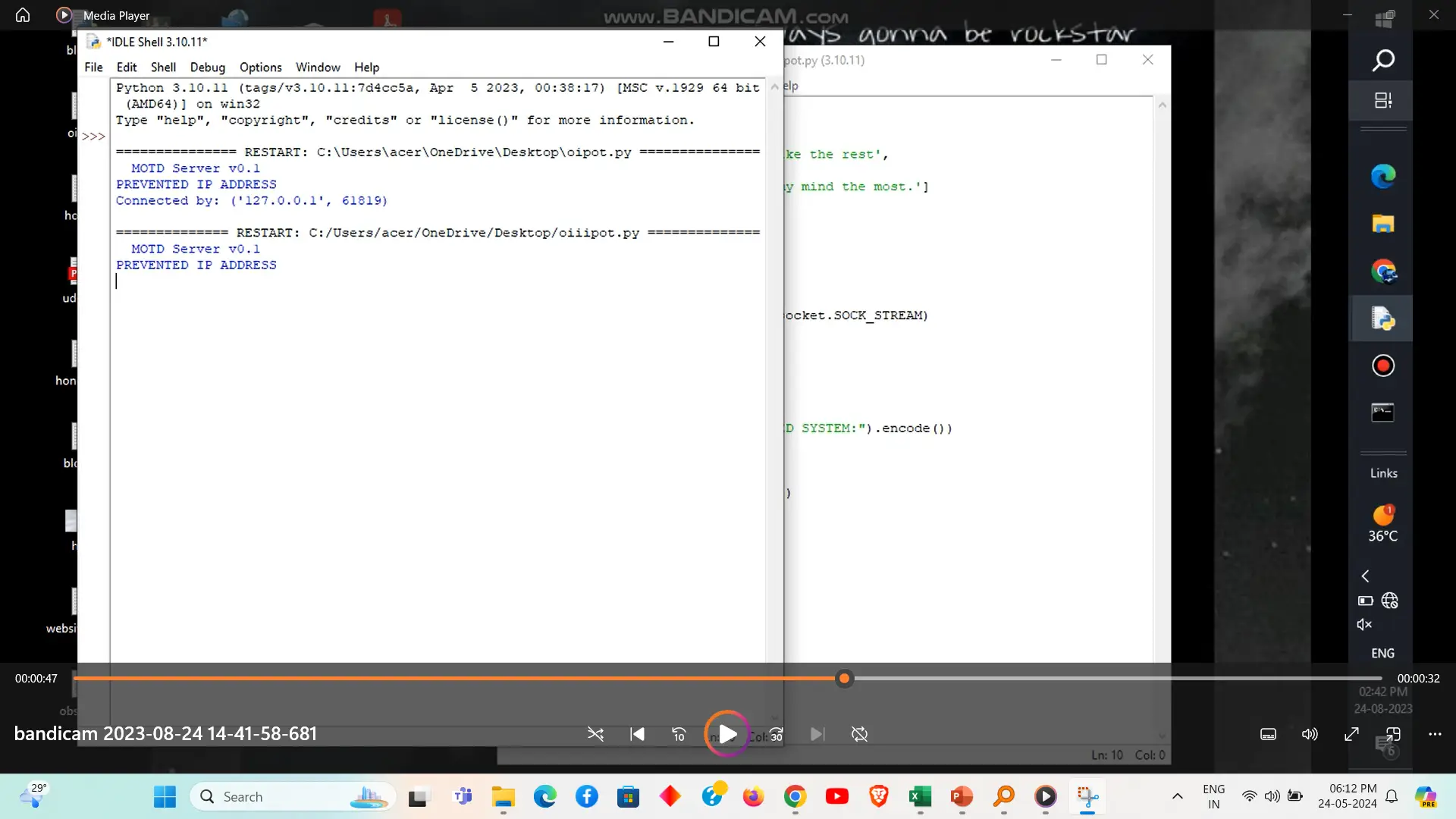
IP address detection using honeypots involves deploying decoy systems designed to attract and monitor malicious activity. When attackers interact with these honeypots, their IP addresses are logged and analyzed, providing valuable information about potential threats. This technique enhances network security by identifying and mitigating malicious actors and understanding their attack methods.
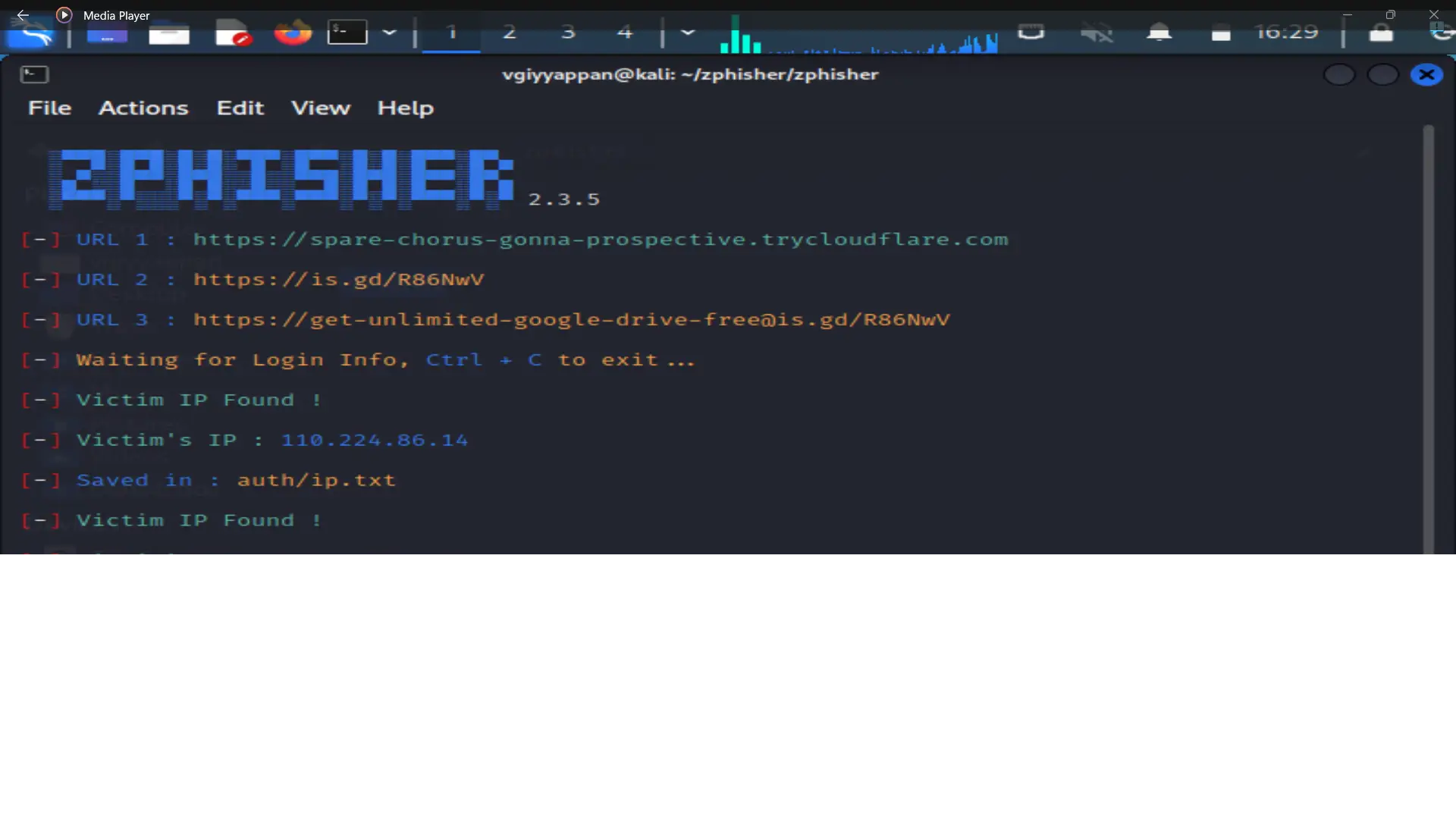
Phishing attacks using ZPHISHER involve deploying a tool that automates the creation of deceptive phishing pages designed to mimic legitimate websites. By tricking users into entering their credentials on these fake pages, attackers can capture sensitive information such as usernames and passwords. ZPHISHER simplifies the process of executing these attacks, highlighting the need for robust security awareness and protective measures.
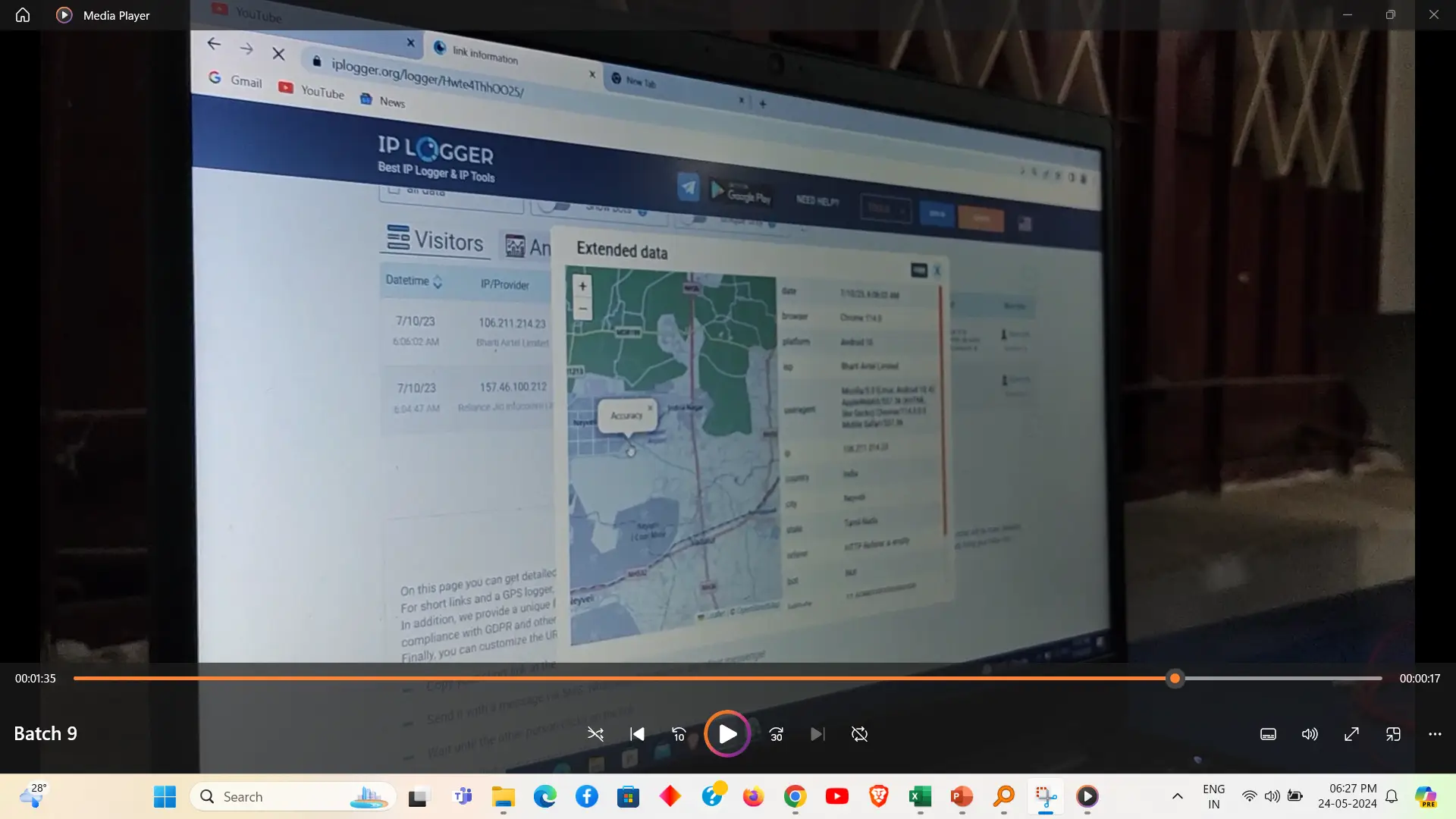
IP tracking using Kali Linux involves employing various network analysis tools and techniques to monitor and trace IP addresses. Tools such as `Nmap`, `traceroute`, and `Wireshark` within Kali Linux can be used to identify active devices, map network paths, and analyse traffic patterns. This capability is essential for network troubleshooting, security assessments, and penetration testing.
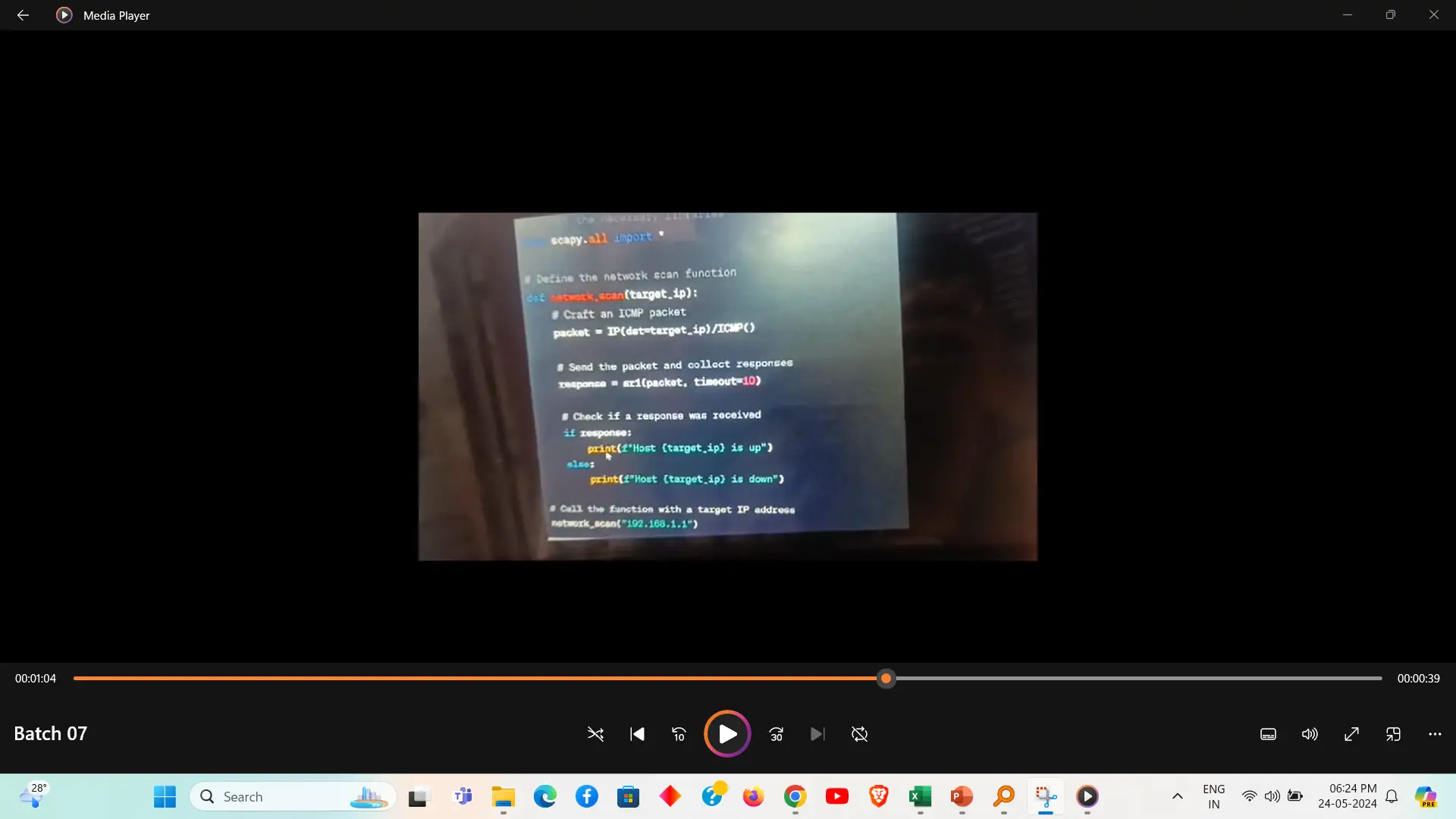
IP address hacking using Kali Linux involves exploiting vulnerabilities or misconfigurations in networked systems to gain unauthorized access. Tools like `nmap` for network scanning, `Metasploit` for exploiting vulnerabilities, and `Hydra` for brute-force attacks can be used to target IP addresses. This process is typically part of a broader penetration testing or security assessment to identify and address weaknesses in a network.
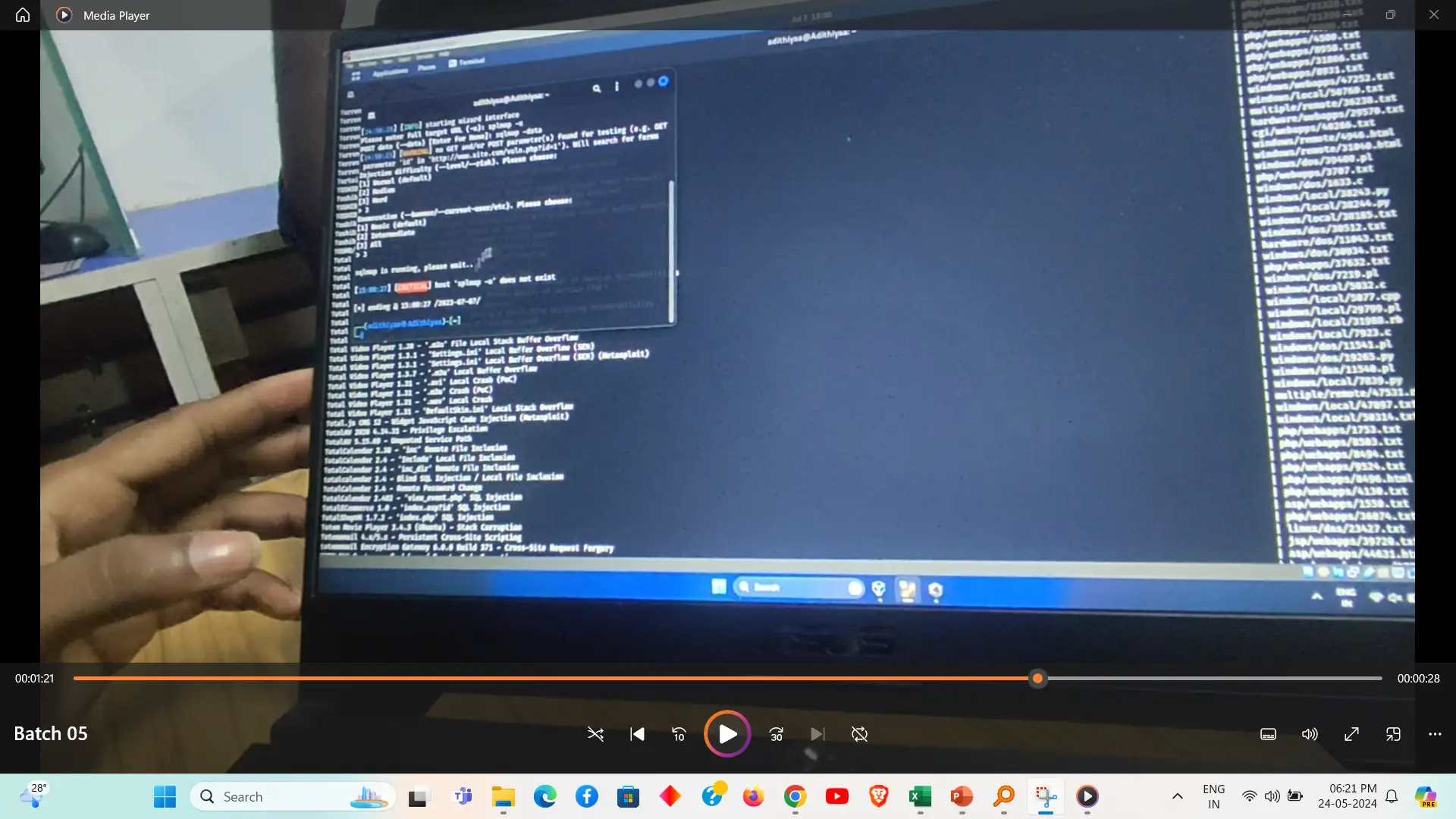
Password attacks using Python involve scripting automated methods to crack passwords by guessing or brute-forcing them. Techniques such as dictionary attacks, brute-force attacks, or hybrid approaches can be implemented using Python libraries and tools like `itertools` for permutations, `hashlib` for hashing, and `requests` or `selenium` for interacting with web forms. These attacks are used in security testing to evaluate the strength of password protection mechanisms.
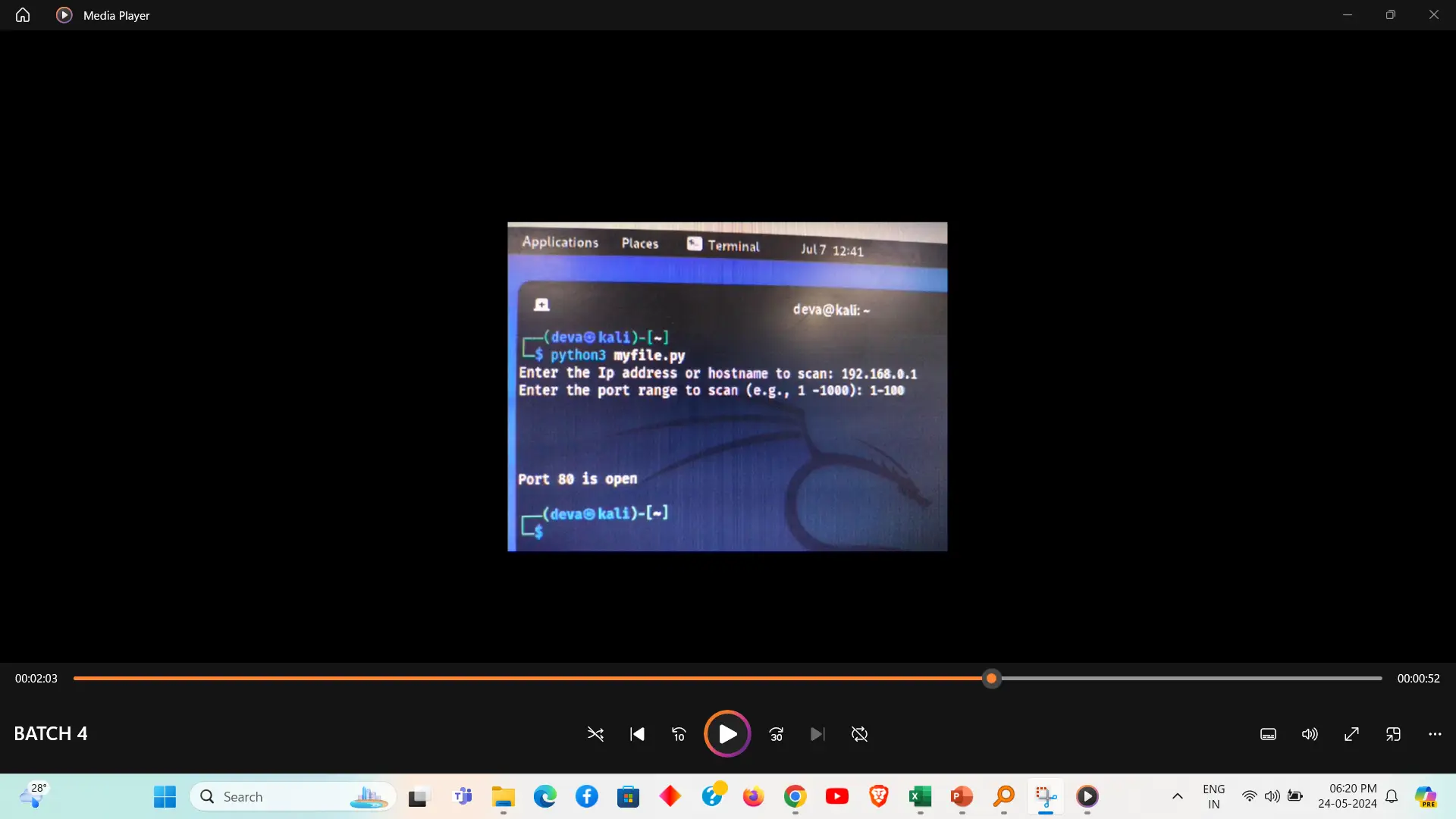
A port scanning attack involves probing a network or system to identify open ports and services running on them. This is often the first step in discovering vulnerabilities that could be exploited. Tools like `nmap` or `masscan` are used to perform port scans, revealing information about potential entry points and weaknesses in a system's security. Effective mitigation includes using firewalls, intrusion detection systems, and regularly updating software to close unnecessary ports.
Information gathering using NMAP involves scanning a network to identify active devices, open ports, and services running on them. NMAP, a powerful network scanning tool, provides detailed information about network hosts, their operating systems, and available services, helping to assess network security and detect vulnerabilities. This process is crucial for network diagnostics, security assessments, and penetration testing.